APT 41 Exploits CVE-2025-8088 for Targeted Espionage in Southeast Asia

APT 41, a China-linked advanced persistent threat group, has been leveraging the recently discovered CVE-2025-8088 vulnerability in WinRAR for espionage campaigns targeting Southeast Asian governments. By exploiting this path traversal vulnerability, APT 41 has been able to execute remote code and deploy custom malware, gaining persistent access to sensitive systems.
Targeted Attacks: Focus on Southeast Asia
APT 41’s primary targets are government and law enforcement agencies in countries like Cambodia, Thailand, and Indonesia. The group delivers malicious payloads through crafted RAR archives, hosted on legitimate cloud services such as Dropbox. These archives exploit CVE-2025-8088, which allows attackers to drop malicious files outside the designated extraction directory and execute them on victim systems.
CVE-2025-8088: Path Traversal Vulnerability in WinRAR
CVE-2025-8088, a path traversal flaw in WinRAR, allows attackers to write files outside the intended directories, such as the Startup folder, ensuring code execution on system reboot. APT 41 uses this flaw to deploy the Amaranth Loader, a custom tool that decrypts and installs additional payloads, including the Havoc C2 Framework, which is used to maintain control over compromised systems.

Source: checkpoint – Triggering CVE-2025-8088.
Geo-Restricted Command and Control Infrastructure
To maintain stealth and minimize exposure, APT 41 uses geo-restricted command and control (C&C) infrastructure, ensuring that their C&C servers are only accessible from targeted regions. The group also utilizes Telegram-based Remote Access Trojans (RATs) like TGAmaranth, which allow them to control compromised systems while evading detection.
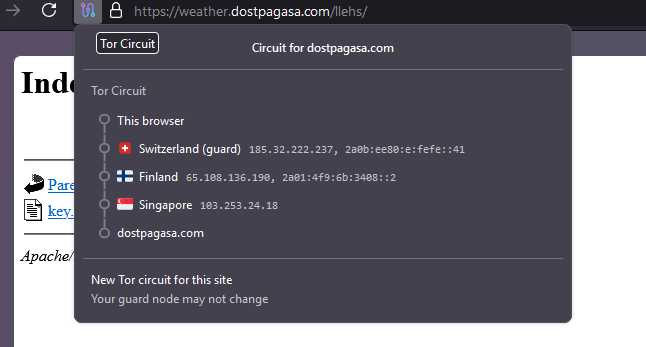
Source: Contacting C&C with an IP from Singapore.
Conclusion: Sophisticated Cyber Espionage Tactics
APT 41’s use of CVE-2025-8088 exemplifies the sophisticated tactics employed by state-sponsored APT groups in cyber espionage. By exploiting zero-day vulnerabilities, deploying custom malware, and utilizing geo-restricted C&C channels, APT 41 has shown advanced capabilities in infiltrating high-value targets. As these attacks continue to evolve, it is essential for organizations to strengthen their defenses against such advanced persistent threats.







No Comment! Be the first one.