SolarWinds Web Help Desk Exploitation Analysis

Internet-exposed SolarWinds Web Help Desk deployments have become entry points for multi-stage attacks, enabling attackers to pivot toward domain controllers and sensitive data. These incidents, noted in December 2025, highlight risks to organizational integrity and confidentiality from unpatched services. Microsoft Defender Research Team investigations reveal reliance on legitimate tools for evasion, underscoring needs for layered defenses.
Attack Chain Overview
Intruders exploited flaws in SolarWinds Web Help Desk to run commands without authentication. Compromised services then launched PowerShell via BITS for payload retrieval. Downloaded files installed Zoho ManageEngine components, granting remote system control.
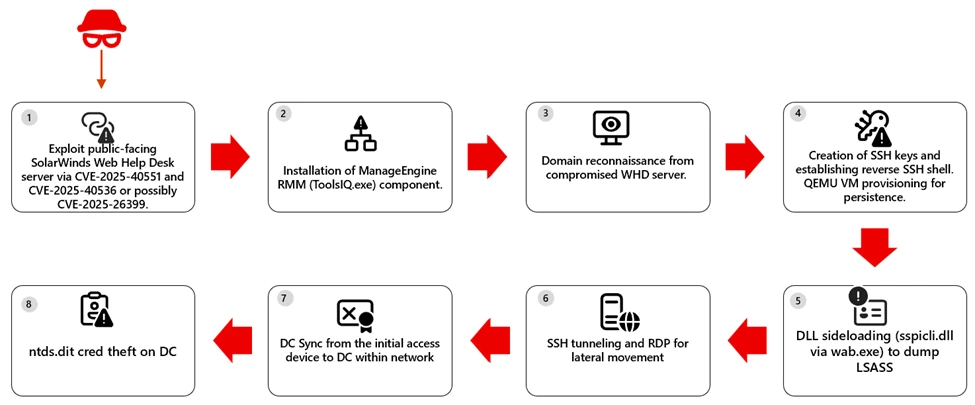
Attackers enumerated domain admins, set up reverse SSH and RDP, and created scheduled tasks for QEMU VMs to mask SSH access. DLL sideloading with wab.exe targeted LSASS for credentials, leading to DCSync on domain controllers in some cases.
Key Vulnerabilities
The intrusions likely involved recent flaws disclosed January 28, 2026, alongside an earlier one, though exact CVEs remain unconfirmed due to overlapping vulnerabilities.
Detection Queries
Security teams can hunt using Microsoft Defender XDR KQL queries. One identifies processes from WebHelpDesk bin spawning suspicious commands like whoami or certutil. Another flags print.exe accessing ntds.dit. A third surfaces vulnerable devices via CVE matches.
| Tactic | Observed Activity | Defender Coverage Example |
|---|---|---|
| Initial Access | WHD exploitation | Possible SolarWinds WHD RCE attempt |
| Execution | PowerShell BITS download | Suspicious Download and Execute |
| Credential Access | LSASS access, DCSync | Suspected DCSync attack |
Mitigation Steps
Organizations should patch CVE-2025-40551, CVE-2025-40536, and CVE-2025-26399 immediately, restrict admin path exposure, and evict unauthorized ManageEngine artifacts like ToolsIQ.exe. Credential rotation and host isolation follow, with enhanced Ajax Proxy logging.
These measures address availability disruptions from exploitation and protect data confidentiality against credential theft. Ongoing analysis may yield further insights.







No Comment! Be the first one.