Apple Pay Phishing Targets Users

Phishing campaigns mimicking Apple notifications exploit user trust in the brand to harvest sensitive Apple ID credentials and payment information. These Apple Pay phishing attempts pose as fraud or billing alerts, creating pressure through high-value transaction claims and urgent action demands. Impacts include potential account compromises affecting service availability and financial confidentiality for millions of users worldwide.
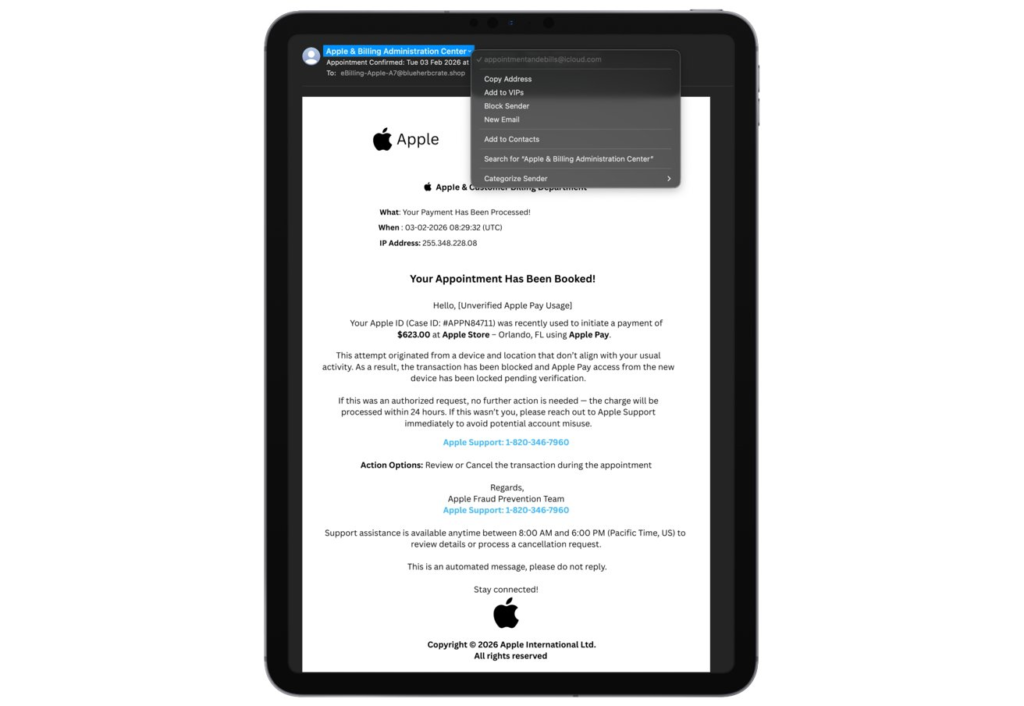
Scam Mechanics
Emails imitate Apple billing support, citing blocked high-dollar Apple Pay purchases at stores, fabricated case IDs, and timestamps. Recipients receive instructions to call provided numbers or attend fake appointments. Callers reach fraudsters posing as support staff seeking verification codes and payment data. Official Apple communications never demand immediate calls or unscheduled visits for billing resolution.
Fraud Indicators
Inconsistencies reveal the deception quickly. Sender domains deviate from apple.com despite convincing display names and logos. Phrasing includes generic greetings like “Hello {Name}” and implausible IP details. Phone numbers link to unrelated searches such as health services upon verification, contrasting Apple’s consistent support channels.
The following table lists common red flags observed in these phishing emails.
| Indicator | Fraudulent Trait |
|---|---|
| Sender Domain | Non-apple.com origins |
| Urgency Language | Immediate action threats |
| Phone Search Results | Unrelated non-Apple pages |
| Greeting Style | “Hello {Name}” placeholders |
No technical vulnerabilities or CVEs enable this social engineering attack.
Verification Practices
Apple maintains transaction histories accessible via device settings or official sites without email prompts. Genuine issues appear directly in these logs.
Protective Measures
Forward suspect messages to Apple’s abuse reporting address before deletion. Enable two-factor authentication and unique strong passwords. Access accounts solely through typed official URLs or apps to bypass phishing traps.
These Apple Pay phishing operations rely on psychological pressure rather than exploits, underscoring risks to personal data integrity and financial availability. Apple provides direct verification channels, eliminating need for unsolicited contacts.






No Comment! Be the first one.