Malicious Chrome Extensions Steal Data

Malicious Chrome extensions pose confidentiality risks by harvesting business data, authentication codes, and browsing activity from legitimate users. Malicious Chrome extensions campaigns include Meta Business Suite scrapers, VK account hijackers, and fake AI assistants, affecting thousands across Chrome Web Store. Extensions abuse broad permissions to export contact lists, analytics, TOTP seeds to attacker infrastructure while masquerading as productivity tools.
CL Suite Extension Capabilities
CL Suite by @CLMasters (jkphinfhmfkckkcnifhjiplhfoiefffl), uploaded March 2025 with 33 installs, claims popup removal and 2FA generation for Meta platforms.
Instead exports TOTP seeds, current codes, Business Manager People CSV, analytics to getauth[.]pro and Telegram channels despite local-only privacy claims.
VK Styles Account Hijacking
Five extensions (ceibjdigmfbbgcpkkdpmjokkokklodmc and variants) affect 500K VK users since June 2025 via GitHub user 2vk’s payloads.
No specific CVEs identified for extension abuse mechanisms.
Extensions use vk[.]com/m0nda profile metadata as dead drops for obfuscated JavaScript from github[.]com/2vk/- repository’s “C” file.
AiFrame Proxy Extensions
32 AI-themed extensions (nlhpidbjmmffhoogcennoiopekbiglbp etc.) with 260K installs embed claude.tapnetic[.]pro iframes for remote control of Readability parsing, speech recognition, Gmail DOM scraping.
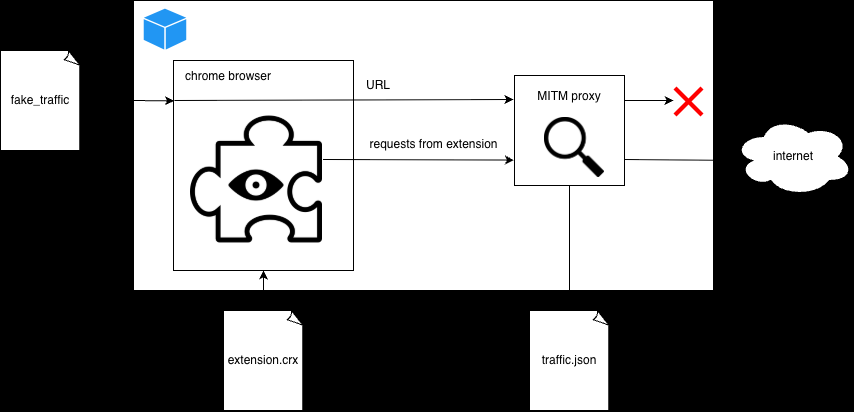
Broader Extension Threat Landscape
Q Continuum identified 287 extensions exfiltrating history to data brokers, representing 37.4M installs or 1% Chrome base.
Malicious Chrome extensions compromise integrity through unauthorized data access and availability via persistent account manipulation. Regular audits, permission reviews, profile separation mitigate risks; no Chrome Store patches noted for identified extensions.





No Comment! Be the first one.