Fake Google Forms Harvest Logins from Job Seekers

Job seekers face heightened confidentiality risks from fake Google Forms campaigns that lure users with employment opportunities to steal account access. These operations exploit trust in legitimate services, spreading via professional networks and email, potentially compromising personal and work data integrity. Victims submitting details encounter credential theft, underscoring the need for domain vigilance in recruitment processes.
Mechanics of Fake Google Forms Phishing
The campaign centers on domains like forms.google.ss-o.com, crafted to resemble forms.google.com while evoking single sign-on legitimacy. Recipients directed to these sites via targeted messages encounter pages replicating Google Forms aesthetics, complete with logos and disclaimers. A fabricated Customer Support Executive job prompt solicits names, emails, and motivations, funneling data to attacker infrastructure.
Personalization occurs through server-side scripts generating unique tracking links per victim. Upon sign-in attempts, traffic shifts to established phishing endpoints like id-v4.com/generation.php, active in prior operations. Redirects to benign Google searches obscure analysis, protecting the operation’s availability for ongoing credential harvesting.
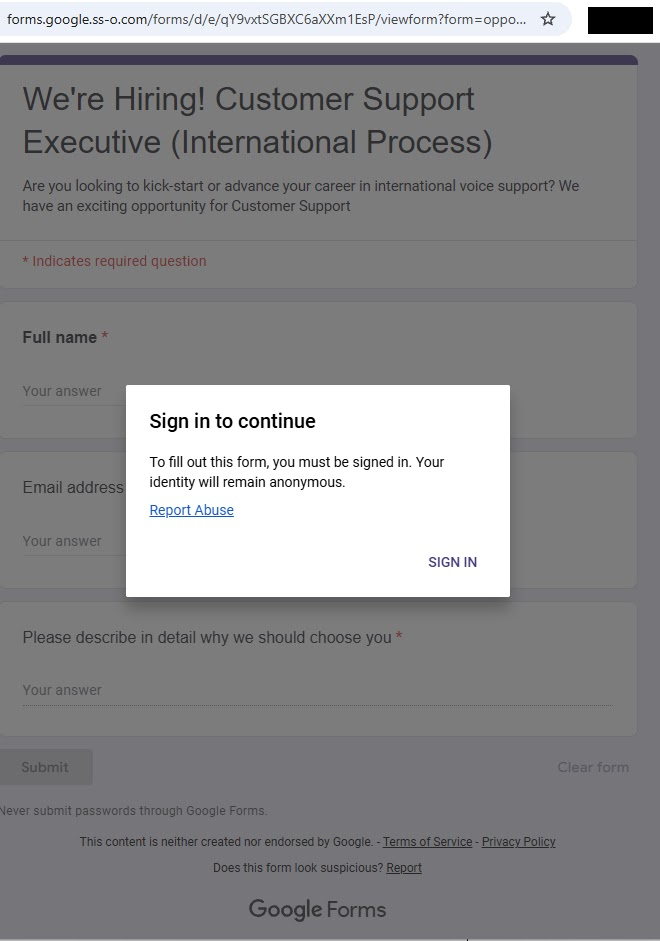
Domain Impersonation and Evasion Tactics
Attackers leverage subdomain tricks where ss-o mimics trusted authentication flows, enhancing perceived integrity. The fake pages maintain visual fidelity to official templates, including standard warnings repurposed to build confidence. This approach bypasses casual scrutiny, enabling sustained access to victim inputs.
The infrastructure employs PHP-based link generation for individualized attacks, complicating detection. One domain faced takedown, but forms.google.ss-o.com persists, indicating adaptive operational resilience. Such fake Google Forms setups threaten availability of legitimate recruitment channels by eroding user trust.
Indicators of Compromise Overview
The following table outlines key domains associated with this fake Google Forms phishing infrastructure.
| Domain | Status |
|---|---|
| id-v4.com | Taken down |
| forms.google.ss-o.com | Active phishing domain |
This table provides essential IOCs for blocking and monitoring efforts against the campaign.
Broader Operational Risks and Defenses
Credential compromise from these fake Google Forms exposes linked services to unauthorized access, risking data exfiltration and account takeover. Job platforms like LinkedIn amplify reach, intersecting professional and personal spheres where confidentiality holds paramount value. Enterprises encounter integrity challenges as stolen logins enable phishing escalation or internal pivots.
Defensive layers include password managers blocking autofill on mismatches, real-time malware scanning for suspicious traffic, and employee training on domain verification. Multi-factor authentication preserves access even post-credential loss, maintaining operational continuity. Unsolicited job links warrant direct employer confirmation, safeguarding against impersonation-driven disruptions.
Phishing via fake Google Forms underscores persistent threats to user authentication flows, compromising confidentiality across individual and organizational boundaries. Availability of trusted services suffers from domain pollution, while integrity demands rigorous verification protocols. Ongoing takedowns reflect collaborative mitigation, yet vigilance remains essential for sustained protection.






No Comment! Be the first one.