Massiv Android Malware Hits Banking via Fake IPTV

Android users seeking IPTV streaming face severe threats from Massiv Android malware, which infiltrates via droppers to seize control of banking functions. Initial campaigns struck Portugal and Greece, with samples from early 2025, extending to Spain, France, and Turkey. This payload jeopardizes financial confidentiality and device integrity through persistent remote access.
Initial Campaigns and Targets
Massiv Android malware emerged in targeted operations against mobile banking in southern Europe, using SMS phishing to push IPTV-themed droppers. ThreatFabric first observed significant activity this year, building on test deployments since January 2025. Victims granting sideloading permissions install payloads that masquerade without altering legitimate IPTV sites, preserving deception.
These attacks prioritize regions with high unofficial app usage, amplifying operational disruptions in personal finance management. Similar Android banking trojan campaigns have proliferated in recent months.
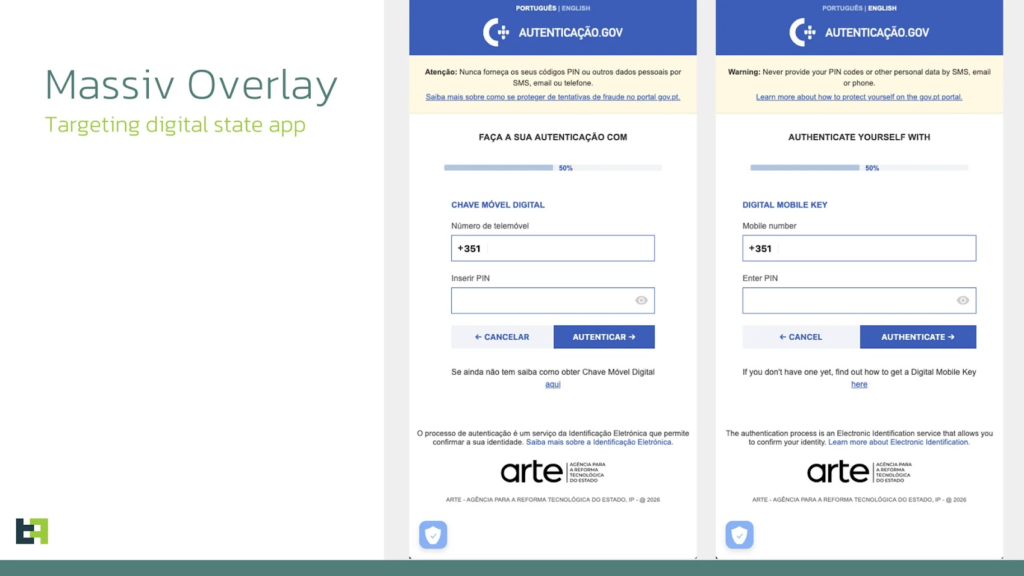
Credential Theft Techniques
The trojan employs screen streaming, keylogging, SMS capture, and dynamic overlays mimicking banking interfaces to harvest credentials and card details. Overlays prompt for sensitive inputs atop legitimate apps, capturing data seamlessly. For Portugal’s gov.pt app, it solicits phone numbers and PINs tied to Digital Mobile Key, facilitating identity misuse.
Captured information supports fraudulent account creation for laundering or loans, bypassing KYC entirely. This erodes trust in public services and financial platforms.
Remote Control and Evasion Features
Operators wield full device dominance via accessibility abuse, deploying black screen overlays to mask navigation while muting alerts. Commands enable clicks, swipes, clipboard edits, screen toggles, pattern unlocks, and settings access like Battery Optimization or Play Protect. Payloads download fresh overlays or APKs dynamically.
Against capture-resistant apps, Massiv Android malware parses UI trees via AccessibilityNodeInfo, compiling JSON of visible elements, texts, coordinates, and states for precise interaction. This resilience sustains control despite protections, threatening prolonged availability.
The table details primary droppers and payloads in Massiv Android malware distributions.
| Package Name | Role |
|---|---|
| hfgx.mqfy.fejku | IPTV24 Dropper |
| hobfjp.anrxf.cucm | Massiv Core |
This table lists confirmed malicious packages for defensive scanning.
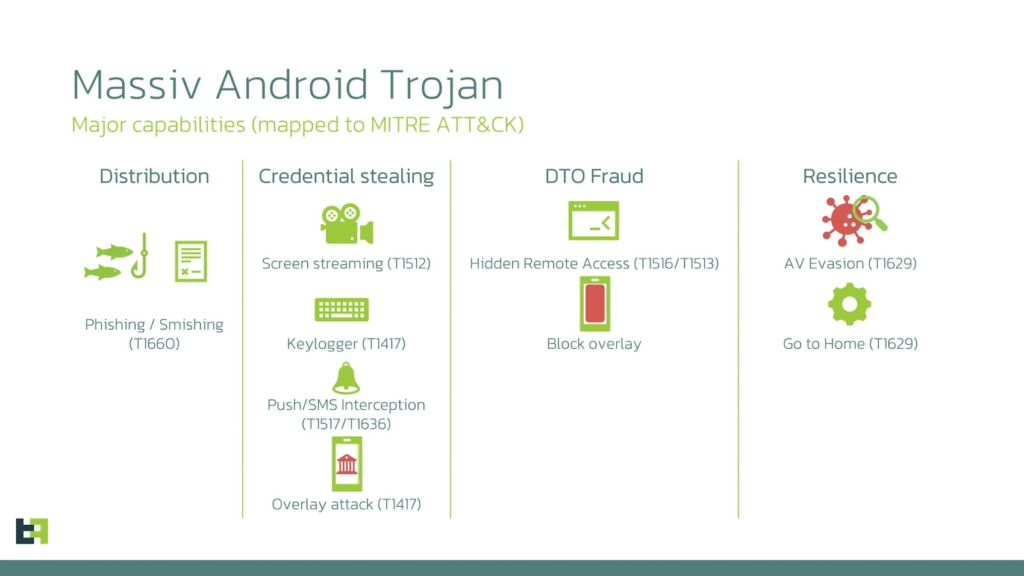
Ties to Broader Banking Trojans
Techniques echo those in Crocodilus, Datzbro, and Klopatra, such as accessibility exploitation and hidden access. API keys in Massiv suggest MaaS evolution, with active coding for expansions. Over six months, TV dropper campaigns dominated Spain, Portugal, France, and Turkey.
IPTV lures mirror escalating mobile phishing trends targeting finance sectors. This positions Massiv amid surging demand for Android financial trojans.
Massiv Android malware inflicts comprehensive compromise, from credential exposure to executed fraud, disrupting personal and economic operations. Confidentiality of banking and identity data falters under remote manipulation, while device availability yields to attacker directives. Sideloading restrictions and permission vigilance counter initial vectors, as observed in vendor guidance.






No Comment! Be the first one.