Gemini AI Powers Malware Stages

Google Threat Intelligence reports threat actors employing Gemini API to produce multi-stage malware, marking expanded AI misuse from reconnaissance to execution. Gemini AI malware technique in HONESTCUE framework, spotted September 2025, queries API for benign prompts yielding compilable C# implementing downloaders. Observed in DPRK, Iranian, PRC, Russian ops probing RCE/phishing/C2 without breakthroughs but boosting efficiency. Framework refines via VirusTotal feedback, limited skills evident.
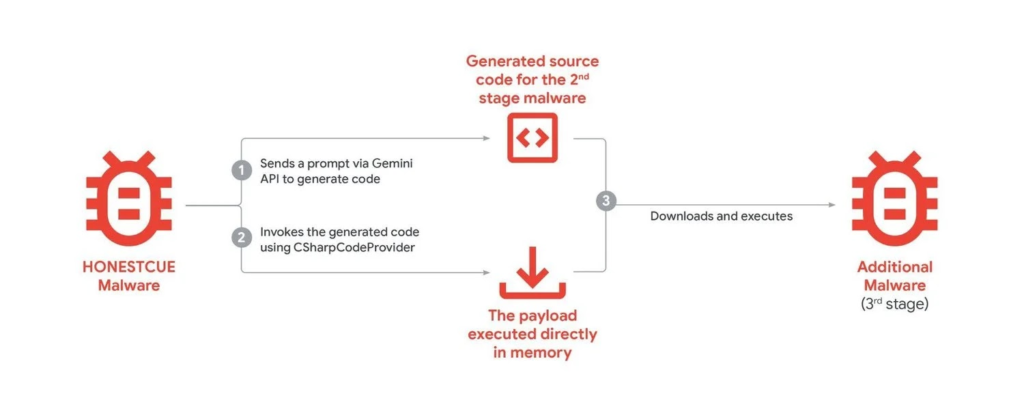
Gemini AI Malware Workflow
HONESTCUE sends static prompts to Gemini, receives self-contained C# classes for stage two like WebClient downloads. .NET CSharpCodeProvider compiles/executes in memory, no disk traces. Stage three pulls payloads from Discord CDN, launches via Process.Start/reflection.
Evasion Techniques Table
HONESTCUE phases employ specific dodges.
| Phase | Evasion Tactic | Detection Challenge |
|---|---|---|
| Stage 1 | Gemini API query | Legit googleapis traffic |
| Stage 2 | In-memory compilation | No disk artifacts |
| Stage 3 | CDN payload fetch | Trusted Discord domains |
APT Gemini Exploitation
GTIG tracked APT31 role-playing researchers for vuln/WAF probes, APT42 phishing scripting, UNC795/APT41 C2. Prompts bypass safeguards as non-malicious dev-like. Xanthorox proxies jailbroken Gemini.
Campaign Indicators
Discord bots, VirusTotal uploads from single account suggest small team PoC. GTIG disrupted via disables/hardening/classifiers; Gemini rejects violations now.
No CVE for API misuse.
Google interventions include account takedowns, model safeguards. Defenders monitor Gemini query volumes, block anomalous traffic, scan .NET loads/Discord fetches from IOCs.
Gemini AI malware accelerates low-skill ops with dynamic payloads, risking confidentiality via undetected exfil and persistence. GTIG IOCs aid hunting; hybrid network/runtime defenses essential.






No Comment! Be the first one.