Malicious Outlook Add-in Steals 4,000 Credentials

A legitimate Outlook meeting scheduler turned phishing tool stole over 4,000 Microsoft account credentials, credit card numbers, and banking security answers after its developer abandoned the project. The Outlook add-in phishing campaign exploited Office add-ins’ remote dynamic dependency model, where Microsoft approves manifests but not live hosted content.
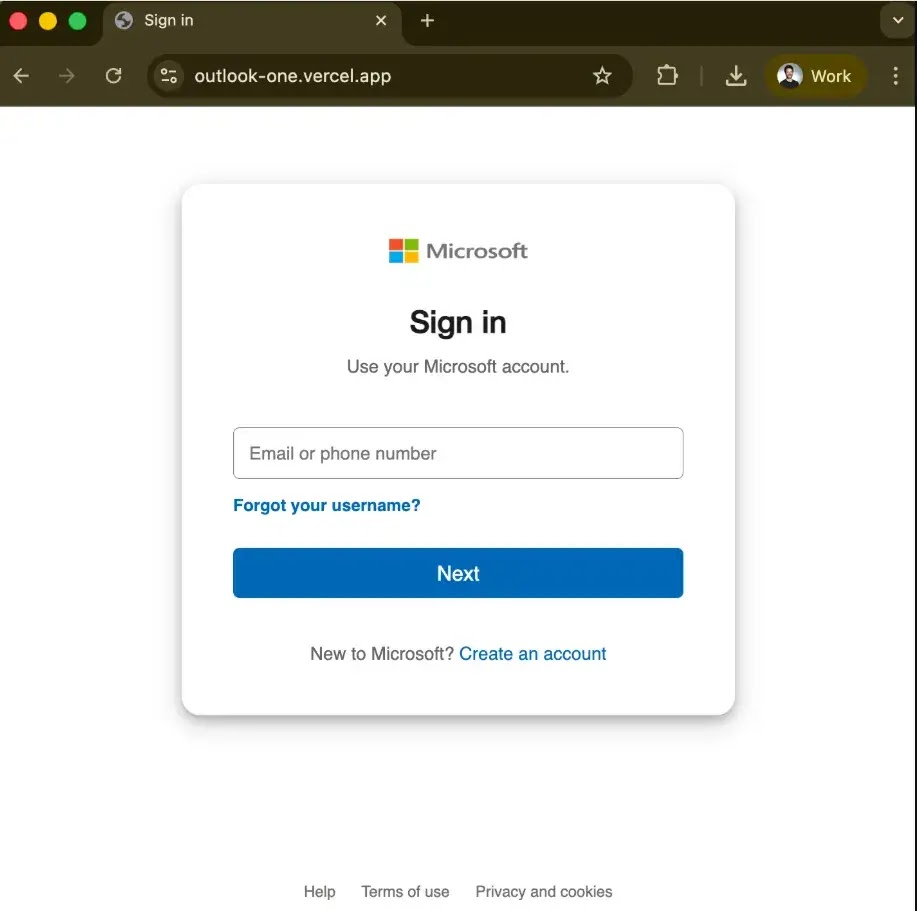
AgreeTo, published December 2022, saw its Vercel domain (outlook-one.vercel.app) claimed by attackers deploying a fake login page served directly in Outlook sidebar to installed users. Koi Security uncovered the operation via exposed Telegram exfiltration, recovering full victim dataset targeting Canadian banks.
Outlook Add-in Phishing Mechanics
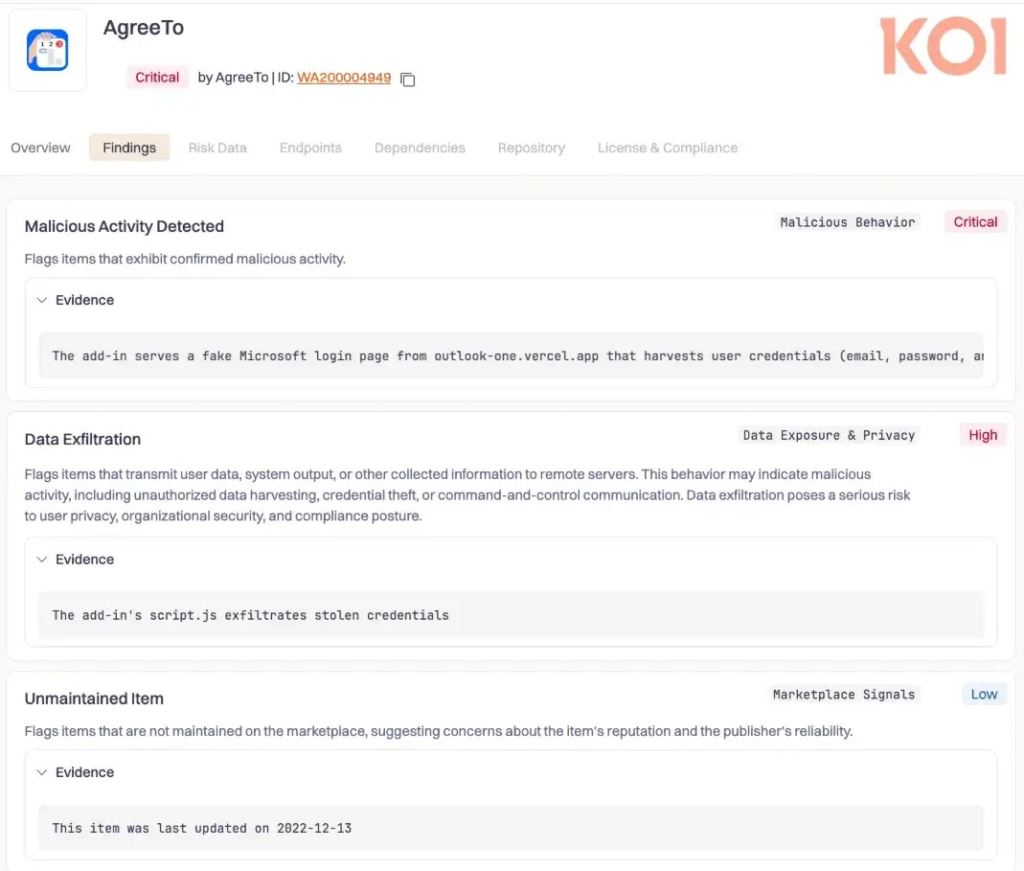
Add-ins load URLs via XML manifests reviewed only at submission; no ongoing verification allows URL hijacking post-abandonment. AgreeTo retained store presence and ReadWriteItem permissions, prompting logins that scripted credentials/IPs to attacker Telegram bot. No email modification observed, focus on credential harvest.
AgreeTo Timeline
December 2022: Legitimate open-source submission to Office Store with positive reviews.
Developer deletes Vercel deployment, orphaning URL.
Attacker registers domain, deploys phishing kit.
Users opening AgreeTo see Microsoft impersonation harvesting banking details.
No CVE assigned to add-in architecture flaw.
Supply Chain Implications
First documented real-world Office add-in compromise highlights orphaned dependency risks in trusted ecosystems. Manifest approval lacks continuous hosting validation, enabling stealthy pivots years later. Permissions like ReadWriteItem grant email access potential, amplifying breach scope.
Victim Impact and Scope
4,000 records include emails, passwords, CC numbers, security Q&As for Canadian institutions. Poor attacker opsec exposed dataset. Microsoft removed add-in post-report.
Mitigation Guidance
Review/remove unused add-ins regularly. Enterprises audit sidebar extensions, monitor for anomalous network from Office apps. Developers secure hosting domains post-support. Microsoft may enhance live content scanning.
Outlook add-in phishing via AgreeTo demonstrates supply chain persistence risks, compromising confidentiality of credentials and financial data in trusted interfaces. Koi AI disclosure prompts ecosystem-wide manifest and dependency reviews.






No Comment! Be the first one.