XWorm RAT Exploits CVE-2018-0802

Phishing campaigns leverage business-themed emails to distribute .XLAM files abusing CVE-2018-0802, delivering XWorm RAT for remote Windows control. XWorm CVE-2018-0802 technique persists since 2022 through Telegram marketplaces, enabling account compromise and data exfiltration.
Fortinet documented multi-stage evasion from OLE shellcode to fileless .NET loaders and process hollowing. Campaign underscores unpatched legacy flaws’ ongoing operational risk across enterprises.
Business-Themed Phishing Lures
Emails themed around payments, purchase orders, shipment docs prompt Excel add-in opens, blending with legitimate correspondence.
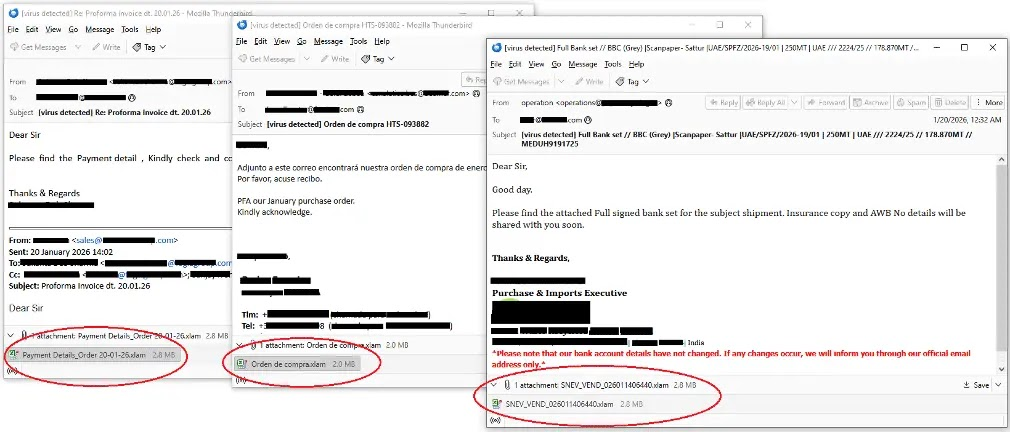
Social engineering maximizes open rates by exploiting routine financial workflows.
Equation Editor Exploitation
Malformed OLE object auto-executes shellcode in EQNEDT32.EXE upon file open, fetching HTA from retrodayaengineering[.]icu/HGG.hta.
| CVE Identifier | Vulnerability Description | CVSS Score |
|---|---|---|
| CVE-2018-0802 | Equation Editor RCE |
This 2018 flaw remains exploitable due to incomplete patching, enabling initial code execution.
HTA PowerShell Transition
Saved as %APPDATA%\VA5.hta, mshta.exe launches Base64 PowerShell extracting .NET module from Cloudinary-hosted jpg between BaseStart/-BaseEnd markers.
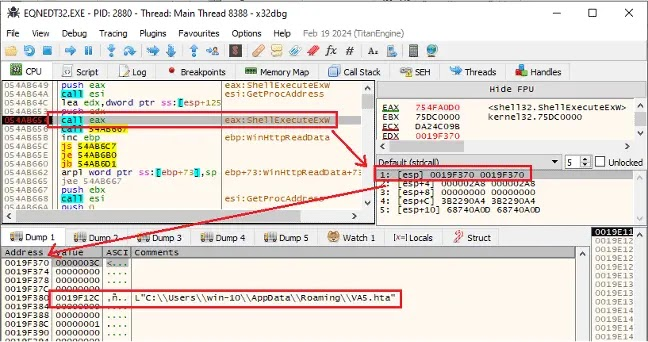
Obfuscation layers complicate static detection during staging.
Fileless .NET Loader
Microsoft.Win32.TaskScheduler-named assembly decodes reversed Base64 URL to pub-3bc1de741f8149f49bdbafa703067f24[.]r2[.]dev/wwa.txt.
Process Hollowing Deployment
Loader reconstructs XWorm in memory, injects via Msbuild.exe hollowing for persistence, decrypts AES config, beacons berlin101[.]com:6000.
RAT Persistence and Evasion
XWorm enables keystroke capture, file ops via encrypted channels. Telegram distribution sustains actor access.
XWorm CVE-2018-0802 chain compromises availability through hollowing, integrity via injection, confidentiality via remote access. Patch Equation Editor per Microsoft advisory, restrict .XLAM/HTA/mshta/PowerShell/Msbuild execution, block observed domains/URLs.





No Comment! Be the first one.