Notepad++ Hijacked by State-Sponsored Hackers
Notepad++, a staple text editor in software development, industrial control systems, and operational technology environments, faced an extended supply chain risk through its update mechanism. The breach exploited a hosting provider’s infrastructure to enable update traffic redirection, undermining the integrity of software distribution channels.
This incident illustrates how third-party hosting failures can compromise availability and confidentiality for widely deployed tools, potentially exposing endpoints to persistent threats without altering the core application.
Attack Timeline and Scope
The compromise surfaced through analysis tied to Notepad++ version 8.8.9, revealing activity from June 2025 until full remediation on December 2, 2025. Security experts noted selective targeting consistent with advanced persistent threat tactics, focusing on users querying the notepad-plus-plus.org update endpoint.
While direct server access ended after provider maintenance on September 2, lingering credentials allowed traffic manipulation until credential rotation in December, affecting update integrity across affected deployments.
Hosting Provider Compromise Details
The former shared hosting provider confirmed suspicious log activity on the server running getDownloadUrl.php until December 1, 2025. Attackers specifically probed for the Notepad++ domain, exploiting known gaps in prior update verification processes.
No evidence emerged of broader client impacts on that server or others, with remediation including vulnerability fixes, credential rotations, and log reviews across the hosting environment, restoring operational availability by early December.
Update Traffic Redirection Mechanics
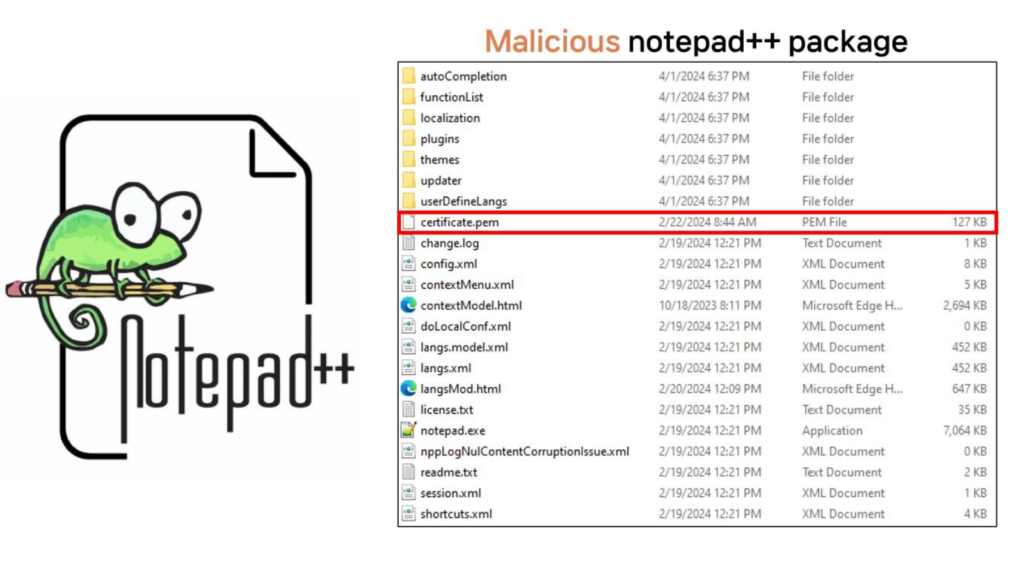
The following timeline table clarifies key phases of the incident based on provider statements and expert analysis.
| Date | Event Description |
|---|---|
| June 2025 | Initial compromise detected; update traffic redirection begins |
| September 2, 2025 | Server maintenance ends attacker direct access |
| November 10, 2025 | Expert analysis notes attack cessation |
| December 2, 2025 | Credential rotation terminates all access; remediation complete |
Remediation and Application Hardening
Notepad++ maintainers shifted to a new hosting provider emphasizing robust security controls. The WinGup updater in v8.8.9 added certificate and signature checks for installers, with XMLDSig signing for server responses enforced in v8.9.2.
These measures ensure future updates resist redirection attempts, bolstering integrity even under network compromise. Users received guidance to manually install v8.9.1 or later from verified sources.
Absence of Specific Indicators
Incident responders analyzed 400 GB of logs without identifying concrete indicators like IP addresses, domains, or hashes. Rapid7 later published complementary findings with additional details, though Notepad++ disclosures remained infrastructure-focused.
Operational Risk Summary
The six-month window exposed Notepad++ users to potential integrity violations via trusted update paths, risking unauthorized code execution in development and OT settings.
Vendor mitigations; hosting migration, enhanced verification, and endpoint updates, eliminated the update traffic redirection vectors, with no post-December activity reported. Organizations should prioritize update validation to mitigate similar supply chain risks in operational environments.


.jpg)



No Comment! Be the first one.